Recently when strengthening security of systems running SSH, While researching best practices and strategies came across the process of “Port Knocking” at https://hackers-arise.com/hacking-with-the-raspberry-pi-getting-started-with-port-knocking/. To simply put it “Port Knocking” is the process of keeping a port closed/blocked unless a specific sequence or input is sent to activate it.
 Installing knockd
Installing knockd
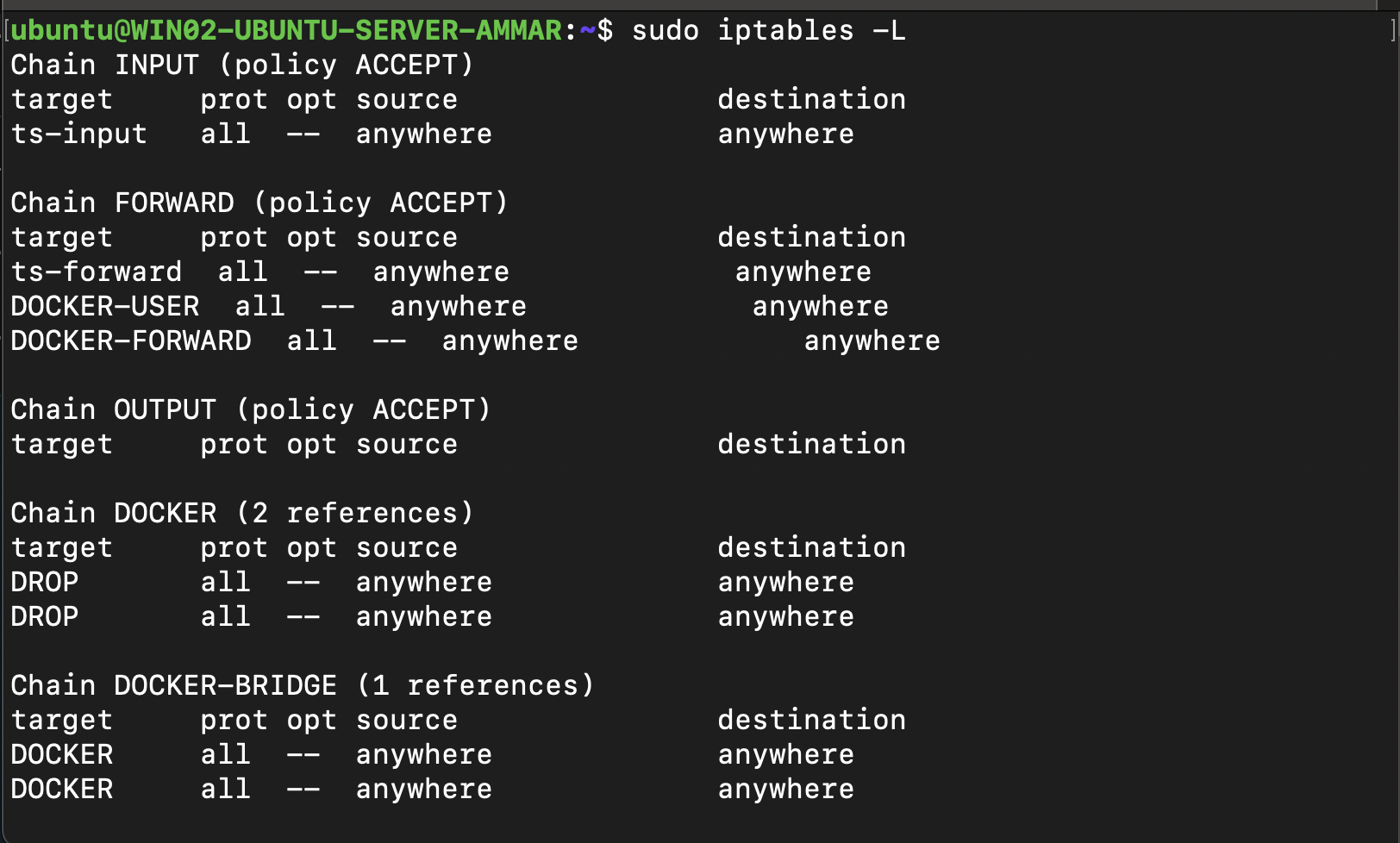 Current rules for iptables
Current rules for iptables
🔐How it actually works:
On the system running the specific service on a port which is open should be blocked/Closed by the firewall eg: iptables. Then using knockd configured with specific sequence numbers which will unblock the respective port if the connection request matches the sequence. The best part is the port is opened to the IP which initiated the correct sequence only and also for a limited time.

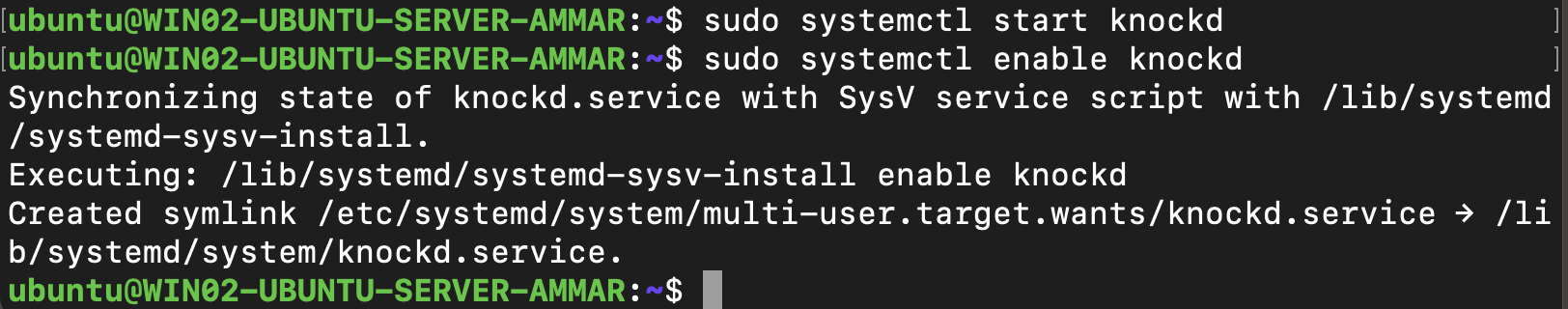 Iptables configured to block ports unless correct sequence using knockd is sent. knockd also enabled on device startup
Iptables configured to block ports unless correct sequence using knockd is sent. knockd also enabled on device startup
Tools used:
SSH - remote access the service we are securing(can be any other service as well eg:smb, http, etc)
Knockd - Tools used to for the main “Port Knocking” process, when sequence done correctly unblocks the port by instructing iptables
Iptables - Powerful firewall/networking tool used to block these ports unless correct knock sequence.
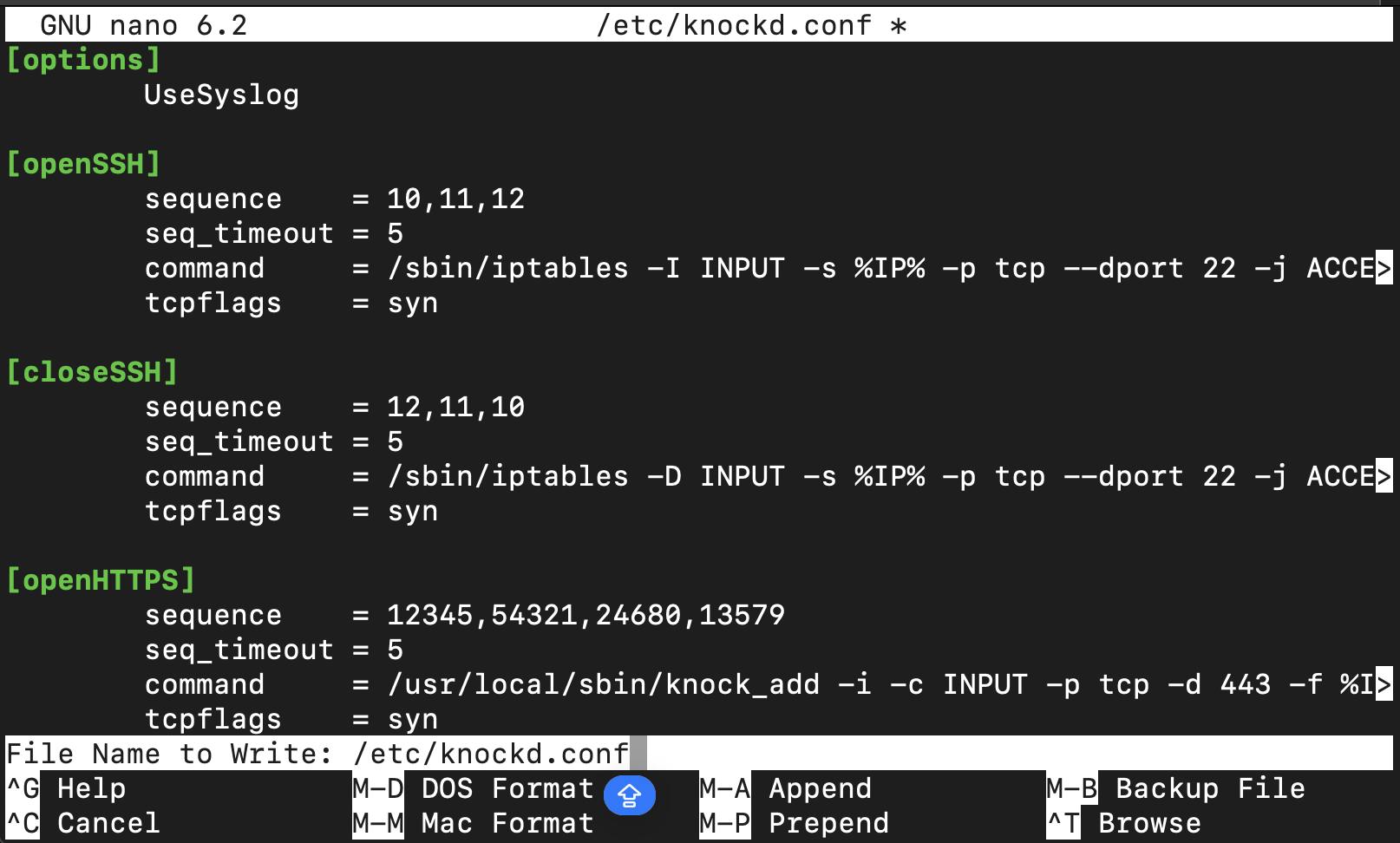 knockd configured for ssh port
knockd configured for ssh port
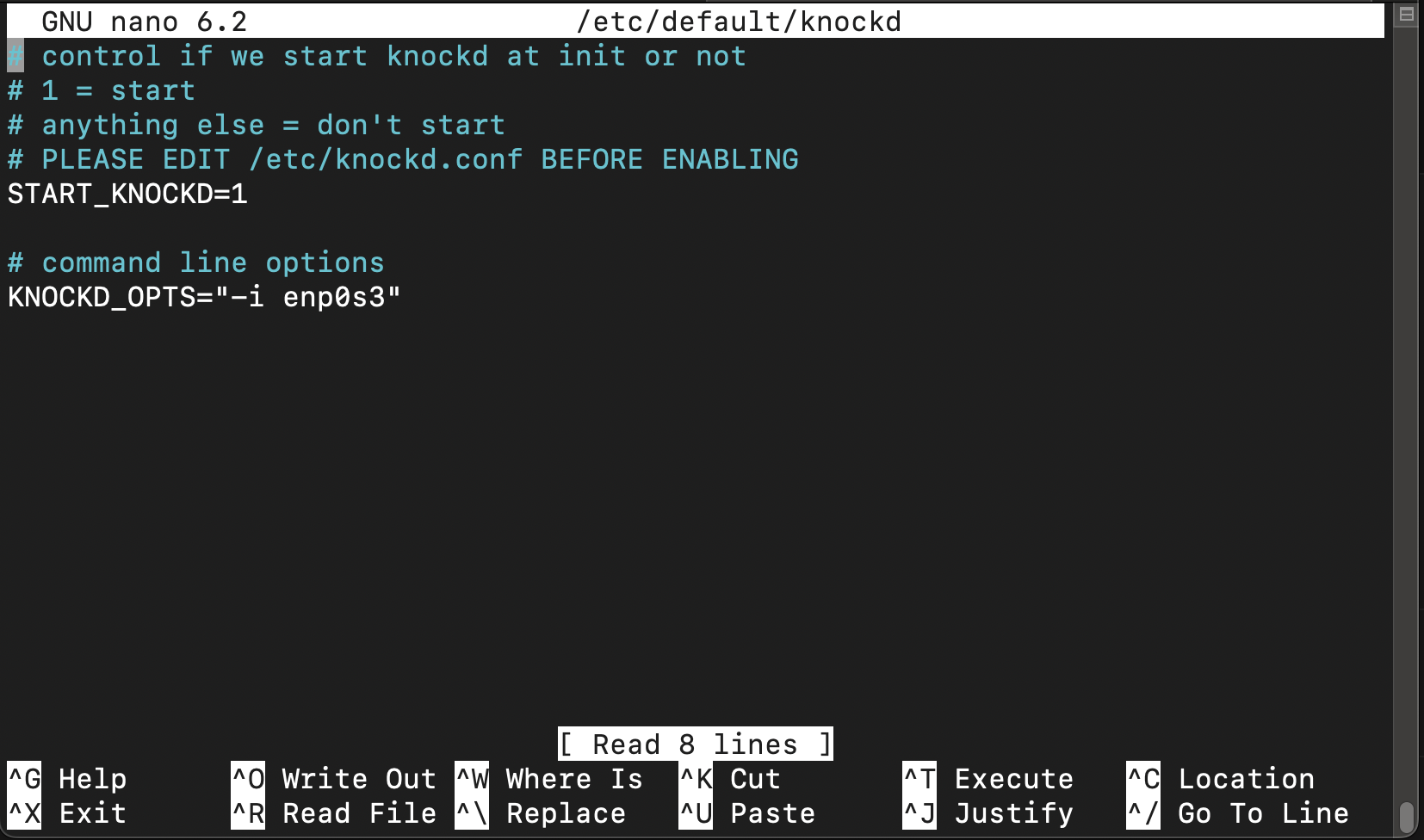 Knockd configured for specific port only so it doesn’t interfere with my tailscale logical adapter the devices which will connect through the tailnet securely
Knockd configured for specific port only so it doesn’t interfere with my tailscale logical adapter the devices which will connect through the tailnet securely
🔍 Testing & Verification:
- Performed nmap scan and ssh port wasn’t open during the scan
- Accessed with Tailscale network it worked, since I didn’t specify the Tailscale logical adapter for port knocking or firewall -tested port knocking and timings
 testing ssh with knock sequence
testing ssh with knock sequence
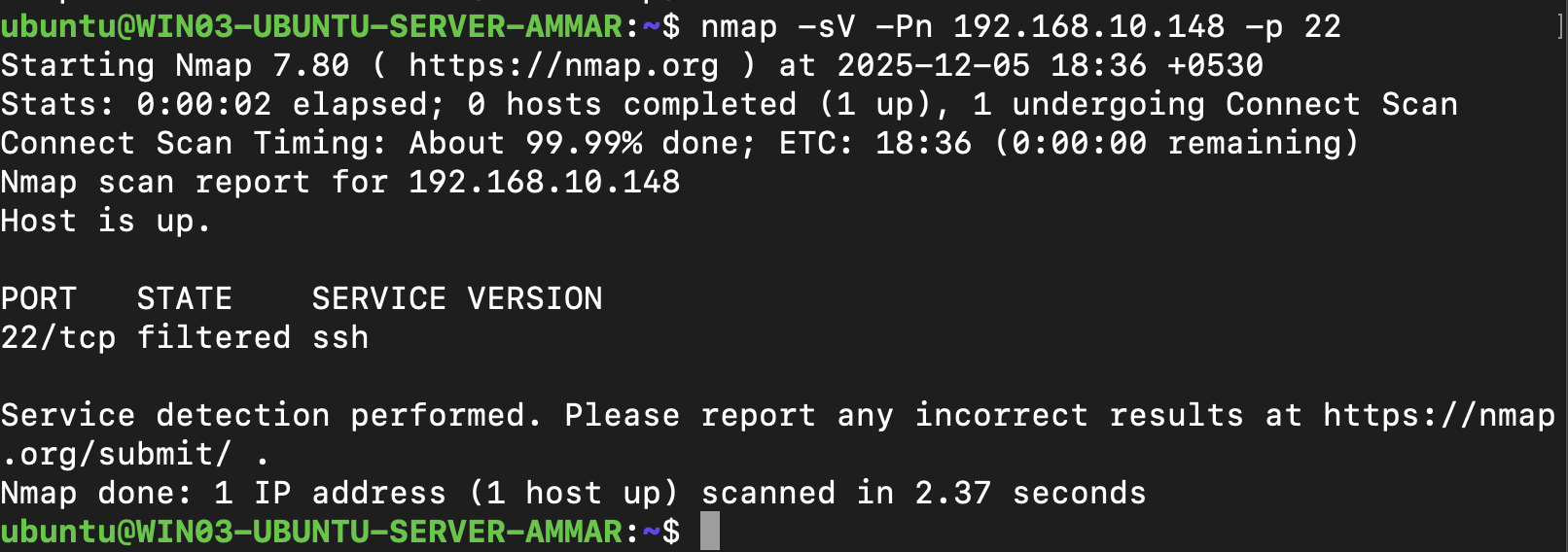 nmap scan on port 22(ssh) succesfully configured!
nmap scan on port 22(ssh) succesfully configured!
💭 Thoughts:
Port Knocking is a great additional layer of security but not necessarily the only step that should be taken. Combining this with key based authentication will do an amazing job. Because port knocking is a very underrated security practice it’s something that not all attackers are aware of, which will be an advantage for us.
 knock package on mac, ssh session initiator
knock package on mac, ssh session initiator
🔐Security Benefits:
SSH port invisible to internet
Zero exposure to port scanners
Prevents brute-force attacks
Lightweight and does not affect performance
❌ Disadvantages:
Bad configuration and insufficient knowledge can lead you locked out of your remote system if no physical access
Additional step to use specific service
Knock sequence can be sniffed on local network
#CyberSecurity #SSH #PortKnocking #Linux #iptables #Networking #Homelab #ServerSecurity #Tailscale #Automation #InfoSec #DevSecOps